반응형
에러해결과정을 스스로 기억하기위해 포스팅합니다.
AWS 서버환경 : Ubuntu, Tomcat9, Nginx(톰캣연동)
Tip: 터미널 창 2개 켜놓고 실행해야함.


✨첫번째 터미널 (Ubuntu 서버 접속후)
certbot 에러 404
ubuntu@:~$ sudo certbot --nginx -d yunamom.duckdns.org
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator nginx, Installer nginx
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for yunamom.duckdns.org
Waiting for verification...
Challenge failed for domain yunamom.duckdns.org
http-01 challenge for yunamom.duckdns.org
Cleaning up challenges
Some challenges have failed.
IMPORTANT NOTES:
- The following errors were reported by the server:
Domain: yunamom.duckdns.org
Type: unauthorized
Detail: Invalid response from
http://yunamom.duckdns.org/.well-known/acme-challenge/JySEiBtvqf8RRcKAbkpPaqAitHPHpY0J7H_ADer58P0
[13.209.236.220]: 404
To fix these errors, please make sure that your domain name was
entered correctly and the DNS A/AAAA record(s) for that domain
contain(s) the right IP address.다음 명령어를 통해 설정을 시작한다.
sudo certbot certonly --manual --email [이메일] -d [도메인]ubuntu@:~$ sudo certbot certonly --manual --email hellokin10@gmail.com -d yunamom.duckdns.org
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for yunamom.duckdns.org
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
NOTE: The IP of this machine will be publicly logged as having requested this
certificate. If you're running certbot in manual mode on a machine that is not
your server, please ensure you're okay with that.
Are you OK with your IP being logged?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Create a file containing just this data:
KPPagWtoBa8rNj8MzIGoRyXwIcEQv0kNcnvtq7blVkA.0Tc284K9HV1X9hq8oXsrv6Xy9c1aiwswFuGgGzK0F2o
And make it available on your web server at this URL:
http://yunamom.duckdns.org/.well-known/acme-challenge/KPPagWtoBa8rNj8MzIGoRyXwIcEQv0kNcnvtq7blVkA
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue여기서 엔터를 누르면 지금 생성값을 만들어주지않았으므로 당연히 404에러가 나온다 그리고 값이 또 리셋되므로
이 터미널창을 그대로 두고 두번째 터미널에서 서버접속을 해준다. (도메인 소유권확인을 위한 작업)
위의 내용은 .well-known/acme-challenge/[임의생성값] 을 호출할 때 아래의 값이 리턴되어야 한다
*아래의 값은 개개인마다 다릅니다 본인의 임의생성값을 확인해야함
KPPagWtoBa8rNj8MzIGoRyXwIcEQv0kNcnvtq7blVkA.0Tc284K9HV1X9hq8oXsrv6Xy9c1aiwswFuGgGzK0F2o
✨두번째 터미널 (Ubuntu 서버 접속후)
톰캣 루트에 폴더/파일 을 만들어준다.
ubuntu@:/var/lib/tomcat9/webapps/ROOT$ sudo mkdir -p .well-known/acme-challenge
ubuntu@:/var/lib/tomcat9/webapps/ROOT$ ls
META-INF hi.html index.html index.jsp sudo
# 숨겨진폴더라 목록에 나오지않는다 ls -a 명령어로 확인할수있다.
ubuntu@:/var/lib/tomcat9/webapps/ROOT$ ls -a
. .. .well-known META-INF hi.html index.html index.jsp sudo
ubuntu@:/var/lib/tomcat9/webapps/ROOT$ cd .well-known/acme-challenge
ubuntu@:/var/lib/tomcat9/webapps/ROOT/.well-known/acme-challenge$ sudo vi KPPagWtoBa8rNj8MzIGoRyXwIcEQv0kNcnvtq7blVkA
ubuntu@:/var/lib/tomcat9/webapps/ROOT/.well-known/acme-challenge$파일 안에 다음을 입력
*아래의 값은 개개인마다 다릅니다 본인의 임의생성값을 확인해야함
KPPagWtoBa8rNj8MzIGoRyXwIcEQv0kNcnvtq7blVkA.0Tc284K9HV1X9hq8oXsrv6Xy9c1aiwswFuGgGzK0F2o접속해서 출력확인후
http://yunamom.duckdns.org/.well-known/acme-challenge/KPPagWtoBa8rNj8MzIGoRyXwIcEQv0kNcnvtq7blVkA
✨그다음 첫번째 터미널 화면으로 돌아가서 엔터를 눌러준다.
Press Enter to Continue
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/yunamom.duckdns.org/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/yunamom.duckdns.org/privkey.pem
Your cert will expire on 2022-07-18. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
ubuntu@:~$그후에 아래 명령어로 SSL 인증서 발급 ( http -> https )
ubuntu@:~$ sudo certbot --nginx -d yunamom.duckdns.org
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator nginx, Installer nginx
Cert not yet due for renewal
You have an existing certificate that has exactly the same domains or certificate name you requested and isn't close to expiry.
(ref: /etc/letsencrypt/renewal/yunamom.duckdns.org.conf)
What would you like to do?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Attempt to reinstall this existing certificate
2: Renew & replace the cert (limit ~5 per 7 days)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Keeping the existing certificate
Deploying Certificate to VirtualHost /etc/nginx/sites-enabled/tomcat.conf
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Redirecting all traffic on port 80 to ssl in /etc/nginx/sites-enabled/tomcat.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://yunamom.duckdns.org
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=yunamom.duckdns.org
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/yunamom.duckdns.org/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/yunamom.duckdns.org/privkey.pem
Your cert will expire on 2022-07-18. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
ubuntu@:~$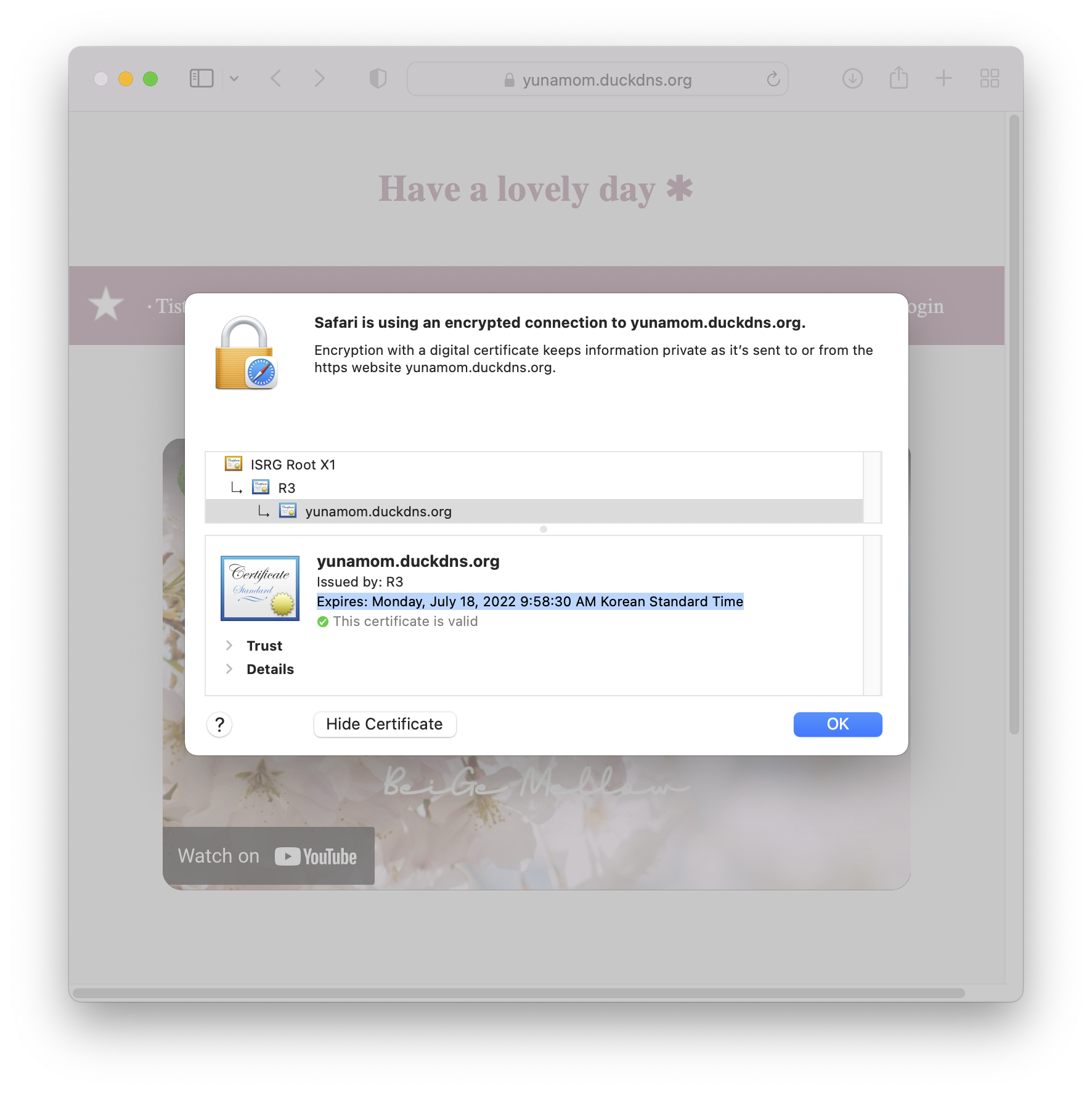
300x250
'서버 > Linux' 카테고리의 다른 글
| To fix these errors, please make sure that your domain name was entered correctly and the DNS A/AAAA record(s) for that domain contain(s) the right IP address. 해결하기 (0) | 2022.07.20 |
|---|---|
| Problem binding to port 80: Could not bind to IPv4 or IPv6. (0) | 2022.07.05 |
| [Linux] certbot 명령으로 인증서 삭제하는방법 (0) | 2022.04.19 |
| [Linux] 리눅스 기본 명령어 (0) | 2022.04.13 |
| [Linux] curl 명령어 사용법 (http/https 관련) (0) | 2022.04.06 |



